A trust architecture includes technologies and methods that aim to protect enterprise data while speeding up digital transformation initiatives and complying with all data privacy-related laws. The increasing prevalence of connected or the internet of things (IoT) devices and companies’ migration to the cloud is pushing organizations to re-assess and validate the credibility of their devices as data expands rapidly across applications, application programming interfaces (APIs), and networks. In addition, the growth of applied AI, 5G, and the metaverse is expected to further accelerate this trend.
Cyberattacks and data thefts have been on the rise in recent years and are posing new challenges by taking advantage of technologies, such as quantum computing, to break encryptions. According to IBM’s Cost of a Data Breach Report 2022, the global average total cost of a data incident is USD43.5mn, up 2.6% from USD4.24mn in 2021. The research also revealed that 83% of the organizations witnessed more than one data breach, and just 17% said that it was their first data breach.
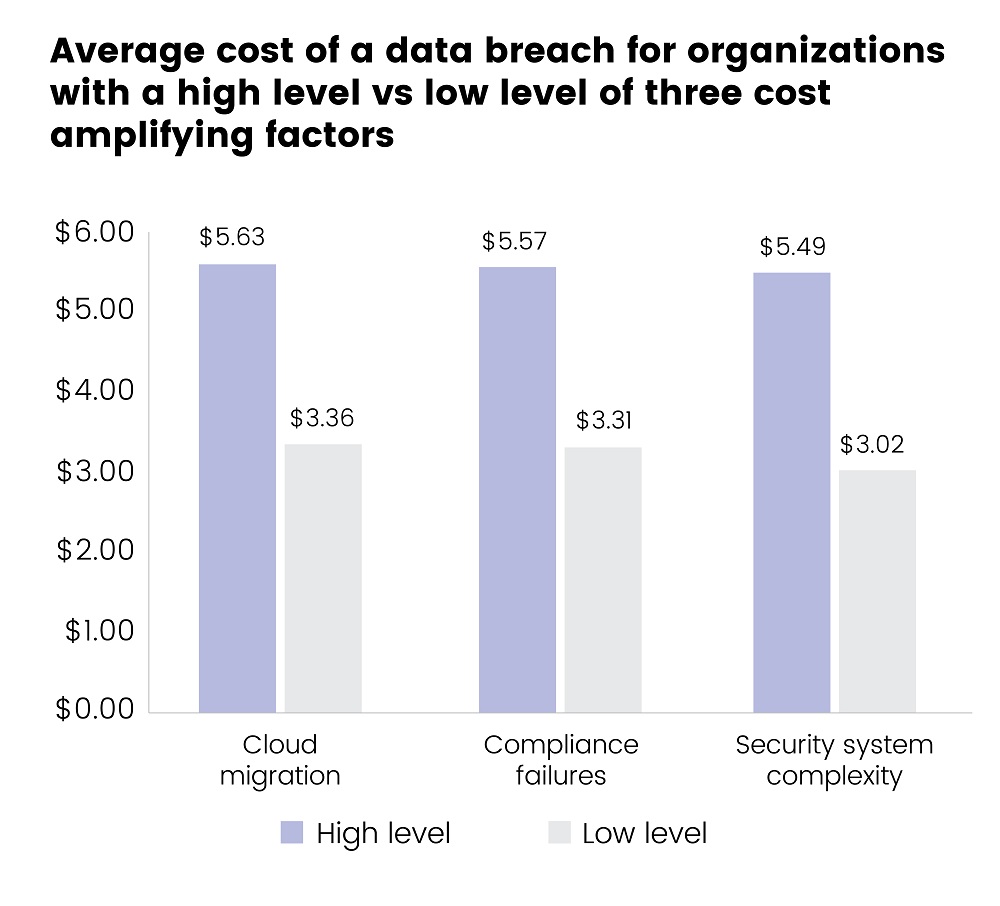
Source: IBM
The above chart suggests that cloud migration, compliance failure, and complexities in the security system were significantly impacted and responsible for increasing the average cost of a data breach. The chart compares organizations with a high and low level of the cost factor and finds the difference between high and low levels of security system complexity to be 58%, that of cloud migration to be 50.5%, and of compliance failures to be 50.9%. The findings also show that organizations with high levels of cloud migration had a USD5.63mn average cost, which was USD1.28mn higher than the average total cost of a data incident, a 25.7% difference.
Technologies Driving Trust Architectures
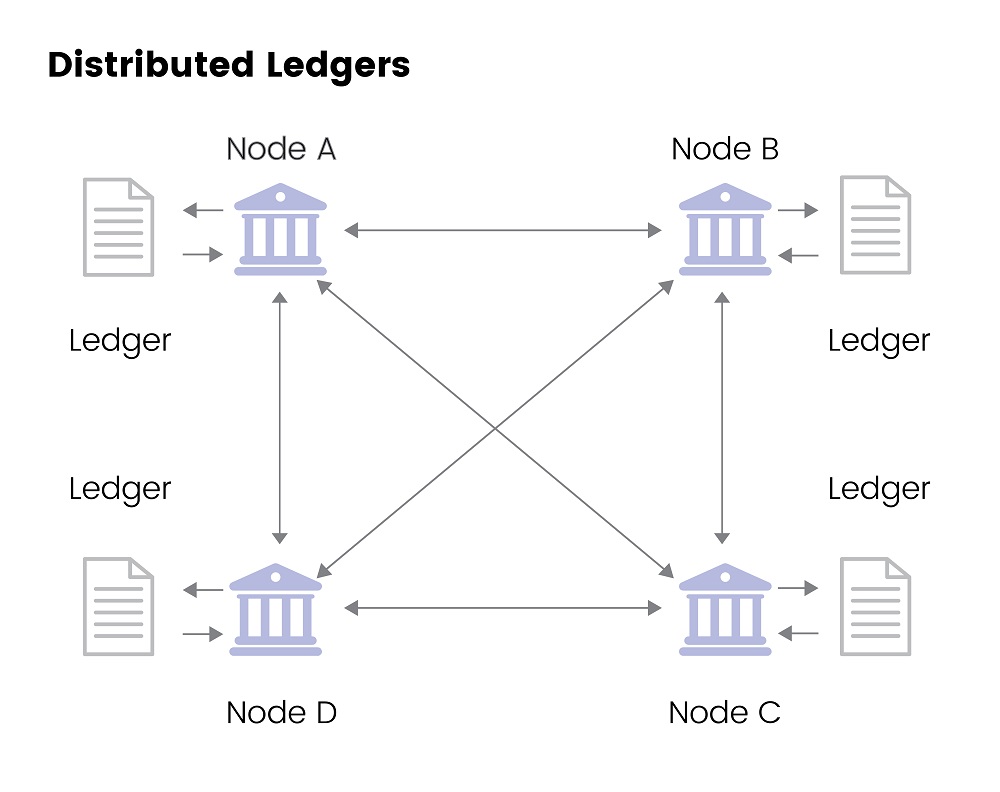
Trust architectures may well incorporate distributed ledger technologies (DLT), blockchain is the most prevalent, and zero-trust security measures that focus on protecting enterprises’ data, services, and identities. While on the one hand, trust architectures lower data theft risks, they also reduce the cost of meeting security regulations, allow lucrative transactions, and minimize expenditures related to cybersecurity.
Cyber risk continues to rise…
Cyber risk, however, continues to threaten some industries, driven by threats of removing intermediaries by distributed ledgers that are generally held and managed by various parties across locations. Moreover, organizations need to focus on the shifting role of regulatory supervision related to the flow of wealth in countries today, as DLT applications usually conflict with the data privacy laws of nations and can, therefore, generate different reactions and acceptance globally.
On a larger scale, this implies that the increase in cyber risks will lead to an extraordinary rise in cybersecurity expenditures, as well as in efforts being applied to monetize and shape trust technologies like highly protected data rooms and cryptocurrency.
Source: CFI Education Inc.
Digital trust technologies enable risk reduction
Digital trust technologies offer more value to organizations and industries leveraging digital technology by creating and preserving the trust of regulators, customers, etc., for using their data, products, and services. Digital trust, thereby, reduces and resolves enterprises’ digital risks across cloud, data, AI and analytics, and risk culture, according to the McKinsey Technology and Trends Outlook 2022 report.
Challenges confronting digital trust…
Digital trust faces specific challenges in a landscape filled with increasing cyberattacks and cyber laws, including:
- the increasing incidence and complexity of cyberattacks,
- increasing expenditures and losses due to these attacks,
- aggressive regulation in the U.S. and worldwide,
- increased dependence on legacy technologies,
- difficult and less predictable AI algorithms, and
- rising scrutiny and uncertainty.

Some of the fast-growing technologies driving trust architectures include:
Zero-trust architecture (ZTA):
The ZTA, Zero Trust Security Model, or Zero Trust Network Access (ZTNA) is a shift in approach from a ‘trust but verify’ to a ‘never trust always verify’ in an organization’s IT security system design. This model promises stronger controls, and everything right from applications, devices, and users within and outside the organization’s network is assumed to be unsafe, as against traditional architecture. As a result, there is less risk from internal threats, leading to reduced costs as losses from cyberattacks are eluded and goodwill enhanced due to fewer data and security breaches.

According to the cybersecurity and cloud services company Akamai, a zero-trust model works effortlessly for users, shields against cyberattacks decreases the attack surfaces for hackers, and streamlines the infrastructure needs of an organization. Three basic principles underlying the model include – default distrust in all entities, minimum-privilege access, and continuous monitoring of security.
Privacy engineering:
Techniques used for overseeing, executing, and maintaining data privacy, including the reduction of risks related to data privacy, assets management, and effecting the use of privacy controls across the organization’s active systems.
Explainable AI (XAI):
Methods employed to understand, trust, and manage emerging AI technologies in the real world, focusing on areas like fairer algorithmic outputs, enhanced transparency, ethics, and efficiency.
Digital identity:
Processes are used to classify and describe individual entities via attributes, such as name, characteristics, etc., in the digital landscape. Digital identity is likely to empower new verification practices and decentralization, according to the McKinsey report.
The road ahead – addressing and adapting to privacy-related concerns and spotting vulnerabilities
Apart from the fact that digital-trust technologies like ZTA, XAI, and privacy engineering cannot be deployed instantly, and new additions to authentication steps can delay an organization’s efficiency, performance, and scalability, data privacy remains a huge concern for industries as emerging Web3 technologies have intrinsic conflicts with the current data privacy regulations. For instance, Europe’s General Data Protection Regulation (GDPR) advocates for people’s rights by allowing them to confer their approvals on the use of their personal data or delete them. On the contrary, blockchain is built on the philosophy of an ‘unchangeable ledger’ that cannot be tampered with and from where data cannot be deleted.
The emergence of modern technologies is also witnessing an essential mistrust between privacy and fairness. While privacy methodologies focus on restricting the collection of personal data, on the one hand, fairness calls for the collection of personal data to identify and settle biases. Concerns over privacy and ethics are also being reviewed around the use, control, and storage of biometric data, while uncertainties and criticism around the Black Box AI, or machine learning (ML) and AI algorithms, are growing.
Several ML systems, particularly deep neural networks, are called black boxes because they cannot be decrypted, implying the Black Box ML model does not offer an explanation to the user or an involved party on how it arrived at an outcome or decision. As a result, novel solutions could face new risks and will also have to adapt to the existing privacy frameworks, fairness, transparency, and ethics.
It is also critical for organizations to detect vulnerabilities, such as inadequate database links, wrongly suspended legacy systems, and violations of third-party affiliates that hackers can exploit. Therefore, companies need to adopt a strong risk-management assessment approach that can be customized to every system to guard against such digital risks.
With a presence in New York, San Francisco, Austin, Seattle, Toronto, London, Zurich, Pune, Bengaluru, and Hyderabad, SG Analytics, a pioneer in Research and Analytics, offers tailor-made services to enterprises worldwide.
A leader in the Technology domain, SG Analytics partners with global technology enterprises across market research and scalable analytics. Contact us today if you are in search of combining market research, analytics, and technology capabilities to design compelling business outcomes driven by technology.

